SELinux (Security-Enhanced Linux) is a security module integrated into the Linux kernel that provides a mechanism for supporting access control security policies. Developed by the NSA, SELinux implements Mandatory Access Control (MAC), which restricts users and processes to only the resources they need to perform their tasks, adding a robust layer of security to the traditional Linux security model.
Key Features:
- Mandatory Access Control (MAC): Unlike Discretionary Access Control (DAC), where users can control the permissions of their files, SELinux enforces security policies that cannot be altered by individual users.
- Policies: SELinux uses security policies to define what processes can access which files, directories, ports, and other resources. These policies are strict and fine-grained, providing detailed control over system behavior.
- Context Labels: Every file, process, and resource in an SELinux-enabled system has a security context, which includes information like user, role, type, and level. These labels determine access based on the defined policies.
- Modes:
- Enforcing: SELinux enforces the security policies and denies access if the policy is violated.
- Permissive: SELinux logs policy violations but does not enforce them, allowing access while administrators debug and refine policies.
- Disabled: SELinux is turned off, and no policies are enforced or logged.
SELinux Components:
- Policies: Collections of rules that dictate access control. Common policies include targeted (the default, which applies to specific services) and strict (which applies to all processes).
- Contexts: Labels applied to files, processes, and other resources that determine their security classification.
- Booleans: Tunable parameters that can be enabled or disabled to adjust SELinux policies dynamically without modifying the policy files.
Basic SELinux Commands:
- Check SELinux Status:
sestatusDisplays the current status of SELinux, including whether it’s enforcing, permissive, or disabled.
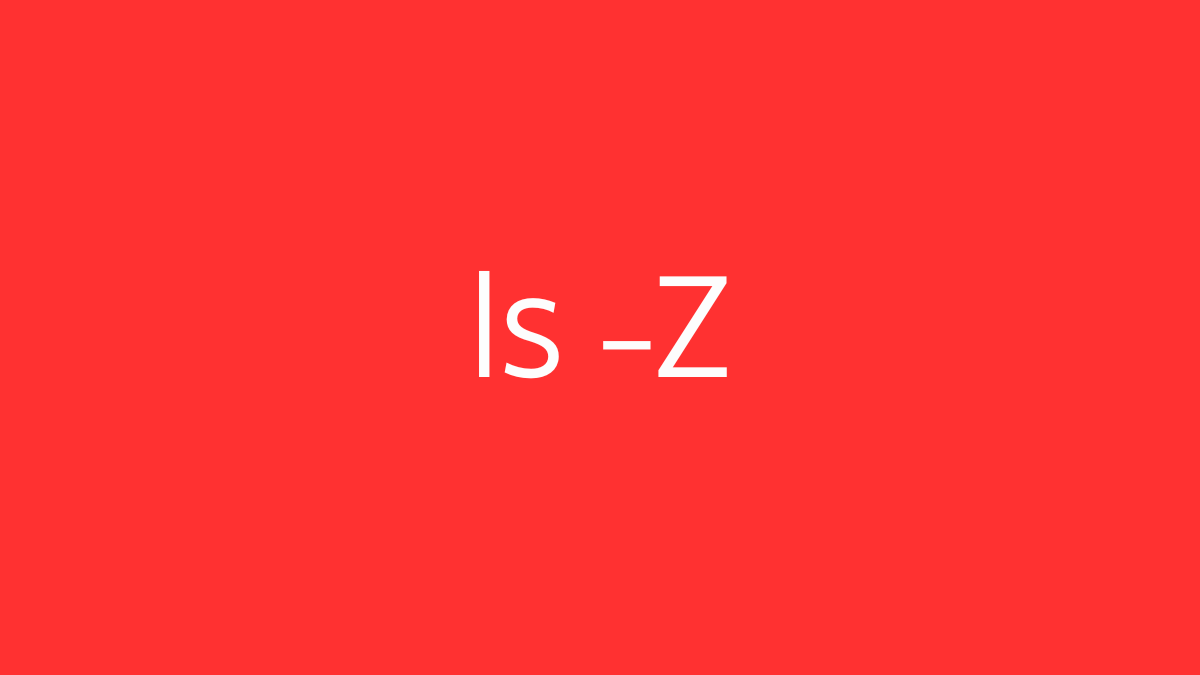
- View Security Contexts:
ls -Z /path/to/directoryLists files with their SELinux security contexts.
- Change Security Context:
chcon -t httpd_sys_content_t /var/www/html/index.htmlChanges the security context of a file (e.g., for use by the Apache web server).
- Enable/Disable SELinux Booleans:
getsebool httpd_can_network_connect
setsebool -P httpd_can_network_connect onEnables or disables specific SELinux booleans, in this case allowing Apache to initiate network connections.
- Switch SELinux Mode:
sudo setenforce 0 # Switch to permissive mode
sudo setenforce 1 # Switch to enforcing modeTemporarily change the SELinux mode between enforcing and permissive.
- Manage SELinux Policies:
- Install SELinux management tools if not already installed:
bash sudo yum install policycoreutils selinux-policy-targeted
Example Use Case:
Imagine running a web server (like Apache) on a SELinux-enabled system. By default, SELinux restricts Apache’s access to specific directories and files to prevent potential security breaches. If Apache is compromised, the attacker’s ability to exploit the system is limited by SELinux policies.
If you need Apache to serve content from a non-standard directory, you would:
- Assign the Correct SELinux Context:
sudo chcon -R -t httpd_sys_content_t /my/custom/directory- Enable the Necessary Boolean:
sudo setsebool -P httpd_can_network_connect onSecurity Considerations:
- Policy Management: Properly managing SELinux policies is crucial. Misconfigured policies can either overly restrict necessary processes or leave security gaps.
- Logging: In enforcing mode, SELinux logs denied accesses, which can be reviewed in
/var/log/audit/audit.logor usingausearchandaudit2allowtools to create custom policies.
Disabling SELinux:
Though not recommended, if you need to disable SELinux:
- Edit the Configuration File:
sudo nano /etc/selinux/configSet SELINUX=disabled.
- Reboot the System:
sudo rebootSELinux is a powerful tool for enhancing the security of Linux systems, particularly in environments where strict access control and security compliance are critical. While it can be complex to configure, the security benefits it provides are substantial.